Introduction to SOAR
Security Orchestration, Automation and Response (SOAR)
SOAR (Security Orchestration, Automation, and Response) is a groundbreaking cybersecurity framework designed to enhance the efficiency, scalability, and effectiveness of security operations. By consolidating and automating disparate security tools, SOAR enables organizations to streamline their workflows, prioritize threats, and respond to incidents with speed and precision.
Importance of SOAR in Modern Cybersecurity

Managing Complex Threats
The complexity of today’s threat landscape demands solutions that can handle large-scale, multi-vector attacks. SOAR’s ability to unify disparate tools and automate repetitive processes ensures organizations are better equipped to handle threats.

Combating Alert Fatigue
With thousands of alerts generated daily, security teams are prone to alert fatigue. SOAR filters and prioritizes these alerts, allowing teams to focus on critical threats.

Regulatory Compliance
Adherence to standards like GDPR, HIPAA, and ISO 27001 is simplified through automated compliance workflows and detailed reporting capabilities.
How SOAR Fits Into the Broader Cybersecurity Ecosystem

Integration with SIEM and EDR
While SIEM aggregates and analyzes data, and EDR secures endpoints, SOAR orchestrates their functionality, creating a holistic incident management process.

Support for Zero Trust
In Zero Trust architectures, SOAR enforces policy compliance and accelerates responses to unauthorized activities.

Cloud Security
As organizations move to cloud environments, SOAR’s adaptability ensures robust security across hybrid and multi-cloud setups.
The primary goals of SOAR are to
1
Enhance Operational Efficiency
Automate manual processes, enabling faster and more accurate responses.
2
Improve Threat Intelligence Utilization
Improve Threat Intelligence Utilization
3
Accelerate Incident Response
Reduce the time to detect (MTTD) and time to respond (MTTR) to incidents.
4
Foster Collaboration
Enable seamless communication among security teams and stakeholders.
How SOAR Works

Integration
SOAR platforms integrate with existing security tools, such as firewalls, SIEM, EDR, threat intelligence feeds, and more. Provides a single interface for monitoring, managing, and responding to threats.

Automation
Predefined workflows handle tasks like alert triage, phishing analysis, and threat containment. Automatically correlates data from multiple sources to identify patterns and detect anomalies.

Incident Management
Predefined response actions that adapt to specific threat scenarios. Tracks incidents from identification to resolution, ensuring accountability and documentation.

Collaboration and Reporting
Facilitates real-time communication and task delegation among team members. Generates insights into incident trends, team performance, and operational gaps.
Key Components of a SOAR System

Security Orchestration
Connects and coordinates various security tools to ensure seamless operations. Eliminates silos by enabling interoperability across the security stack.

Automation
Automates repetitive, time-consuming tasks, freeing up security personnel for strategic initiatives.Examples include automated malware analysis, URL blocking, and sandboxing suspicious files.

Incident Response
Employs standardized workflows and playbooks for handling incidents.Ensures quick containment, eradication, and recovery from threats.

Threat Intelligence
Aggregates data from multiple threat feeds. Enriches alerts with context, improving prioritization and response accuracy.

Case Management
Tracks incidents and their resolutions. Provides a comprehensive audit trail for compliance and analysis.

Analytics and Reporting
Provides visual analytics to track security posture, measure response times, and identify areas for improvement. Offers insights into incidents to refine detection and response processes over time.
Why You Must Opt for Our SOAR
Unmatched Expertise
Tailored Solutions
Proactive Threat Management
Scalability and Reliability

Unmatched Expertise
At Codeguardian.ai, our SOAR solutions are built on years of experience and innovation. We combine cutting-edge technology with an elite team of experts to deliver superior results.
How We Ensure Security & Confidentiality of SOAR
Data Security
All data is encrypted during transmission and at rest. Role-based access management to ensure only authorized personnel have access.
Compliance
Adheres to global regulatory standards like GDPR, HIPAA, and ISO 27001. Regular audits and assessments to maintain compliance.
Secure Development Practices
Follows secure coding standards and performs rigorous testing to minimize vulnerabilities.
Approach for SOAR

Assessment
Analyze current security posture, tools, and workflows. Identify gaps and areas for improvement.

Customization
Design tailored playbooks and integrations. Develop a roadmap for implementation.

Deployment
Implement the SOAR platform with minimal operational impact.Ensure seamless integration with existing tools.

Training
Provide hands-on training for security teams to maximize platform capabilities.

Optimization
Continuously monitor and refine workflows based on feedback and evolving threats.
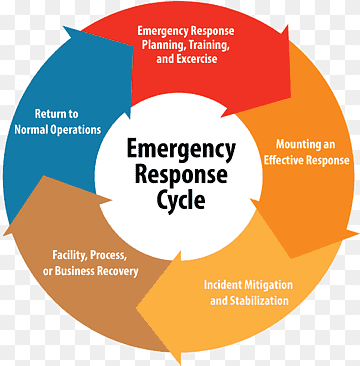
Define Incident Response Processes
Align SOAR playbooks with existing incident response policies and procedures.
Clearly define who is responsible for monitoring, responding, and escalating incidents.
Methodology for SOAR
Discovery
Conduct a thorough analysis of the organization’s security needs and infrastructure.
Design
Develop customized workflows and integration strategies.
Implementation
Deploy the solution in stages to minimize disruption.
Testing
Perform rigorous testing to ensure functionality and reliability.
Optimization
Continuously refine the system to adapt to new challenges and requirements.
Applicability
Industries
Financial Services Healthcare Government Retail Technology Manufacturing
Use Cases
Phishing Mitigation Ransomware Response Vulnerability Management Insider Threat Detection Compliance Reporting
Post-Incident Analysis
Facilitates forensic analysis and post-incident reviews to refine processes and enhance overall security posture.
Operational Efficiency
Reduces operational overhead by automating routine tasks, allowing security teams to focus on strategic initiatives.
Risk
1
Implementation Challenges
Integrating SOAR with legacy systems may require significant effort. Ensuring compatibility with diverse tools can be complex.
2
Over-Reliance on Automation
Human oversight is essential to validate automated actions and prevent errors.
3
Data Privacy Concerns
Misconfigurations could expose sensitive data if not properly managed.
4
Integration Challenges
Difficulty in integrating SOAR with legacy systems or tools lacking robust APIs. Potential for misconfiguration during integration, leading to incomplete data flows or inefficiencies.
Key Features
Multi-Tool Integration
Dynamic Playbooks
Real-Time Reporting
Advanced Analytics
Collaboration Tools

Multi-Tool Integration
Connects with SIEM, EDR, firewalls, and more.
Benefits

Operational Efficiency
Automates time-consuming tasks, allowing teams to focus on strategic goals.

Improved Response Times
Rapid detection and mitigation of threats reduce downtime and damage.

Cost Savings
Reduces operational costs by optimizing resource utilization.

Enhanced Visibility
Unified dashboards provide a comprehensive view of security operations.
Integration Capabilities

Prebuilt connectors for leading security tools like Splunk, Palo Alto, and Microsoft Defender.
API-driven integrations for custom applications.
Native support for cloud platforms like AWS, Azure, and Google Cloud.
Deployment Options
On-Premises
Ideal for organizations with strict data sovereignty requirements.
Cloud-Based
Offers scalability and flexibility, reducing infrastructure costs.
Hybrid
Combines the best of on-premises and cloud for maximum versatility.
Managed Service Provider (MSP) or Managed Security Service Provider (MSSP)
A third-party provider manages and operates the SOAR platform on behalf of the organization.
SaaS (Software as a Service)
SOAR is offered as a subscription-based service, with the provider managing all aspects of hosting and maintenance.
User Experience
Intuitive Dashboards
SOAR platforms provide a single-pane-of-glass view, consolidating data from various tools, allowing users to monitor security incidents, workflows, and system performance in real-time. Dashboards can be tailored to specific roles or functions, ensuring that analysts, managers, and executives have access to the most relevant information.
Streamlined Workflows
Creating, modifying, and deploying workflows is made simple through visual editors. Alerts are automatically categorized and prioritized, reducing the cognitive load on security teams. Step-by-step instructions assist even less experienced analysts in handling complex incidents.
Collaboration Features
Enables teams to share insights, updates, and actions directly within the platform. Assign specific tasks to team members, ensuring accountability and clarity during incident resolution. Virtual environments where teams can collaborate in real-time during critical events.
User-Centric Design
• Ease of Use: Designed with the end-user in mind, SOAR platforms minimize the need for extensive training. • Accessibility: Web-based interfaces ensure access from any device, supporting remote and hybrid work environments. • Role-Based Views: Provides access and functionalities tailored to the user’s role, from SOC analysts to CISOs.
Real-World Case Studies
Case Study 1:
Financial Institution
A major bank faced overwhelming alert volumes and struggled with slow incident response times. Implemented SOAR to integrate their SIEM and threat intelligence tools.
Case Study 2:
Healthcare Organization
A healthcare provider required a secure, efficient system to manage sensitive patient data and comply with HIPAA regulations. Deployed a SOAR platform with robust playbooks for ransomware mitigation and insider threat detection.
Case Study 3:
Retail Enterprise
A global retailer experienced frequent breaches targeting their e-commerce infrastructure. Leveraged SOAR to integrate cloud security tools and automate incident response workflows.
Support and Maintenance

24/7 Monitoring and Assistance
Our SOAR solution is backed by a dedicated support team available around the clock to resolve any issues or queries.

Regular Updates
Frequent updates introduce new functionalities, integrations, and optimizations to stay ahead of evolving threats.

Comprehensive Documentation
Step-by-step manuals to help users maximize the platform’s potential A repository of FAQs, troubleshooting tips, and best practices.

Customizable Support Plans
Includes email and ticket-based support during business hours. Offers priority response times, dedicated account managers, and on-demand assistance.

Integration Maintenance
Ensuring seamless integration with connected tools (e.g., SIEM, endpoint protection, firewalls) as these tools evolve.
Updating APIs and connectors to support new features or address changes in integrated systems.
Security and Privacy

Data Protection
Utilizes AES-256 encryption for data at rest and TLS for data in transit. Sensitive data is anonymized in logs and reports to enhance privacy.

Access Control
Ensures that users only have access to data and functionalities relevant to their roles. Adds an extra layer of security for user accounts.

Platform Security
Implements continuous verification of users and devices. Ensures the platform is resilient against known and emerging threats.

Compliance
Protecting personal data and ensuring privacy. Safeguarding healthcare information. Adhering to global information security management standards.

Incident Response and Recovery
Ensures data integrity and availability in case of an attack. Automated processes for notifying stakeholders in compliance with regulations.
Frequently Asked Questions (FAQs) About SOAR
What is SOAR, and how does it differ from other cybersecurity tools?
SOAR (Security Orchestration, Automation, and Response) is a comprehensive solution that unifies and automates security operations by integrating diverse security tools, automating repetitive tasks like alert triage, and enabling dynamic incident response through customizable playbooks. Unlike SIEM (Security Information and Event Management), which focuses on collecting and analyzing security data, SOAR acts as a central hub for orchestrating and automating actions across multiple tools. In contrast to EDR (Endpoint Detection and Response), which primarily protects endpoint devices, SOAR provides a broader scope by coordinating and streamlining security actions across an entire ecosystem.
Why is SOAR important for modern cybersecurity?
Automates prioritization of thousands of alerts, allowing teams to focus on high-risk incidents. Simplifies complex workflows, making it accessible for less experienced analysts. Reduces time-to-detect (MTTD) and time-to-respond (MTTR) to threats. Handles increasing alert volumes as organizations grow and adopt new technologies.
What are the key components of a SOAR platform?
Connects and coordinates multiple tools to work in unison. Executes predefined workflows for repetitive tasks. Tracks and resolves incidents with structured playbooks. Aggregates and enriches data from various sources. Provides a centralized system for tracking and documenting incidents.
How does SOAR integrate with existing tools?
SOAR platforms leverage APIs, prebuilt connectors, and custom scripts to integrate with various tools across the security ecosystem, including SIEM solutions (e.g., Splunk, IBM QRadar), endpoint security tools (e.g., CrowdStrike, Microsoft Defender), firewalls, IDS/IPS, and threat intelligence platforms. These integrations enable SOAR to pull data, correlate information, and automate responses seamlessly.
Can SOAR handle compliance requirements?
Yes, SOAR simplifies compliance by automating the collection of audit logs, providing standardized reports aligned with frameworks like GDPR, HIPAA, and ISO 27001, and enforcing consistent policies through orchestrated workflows.
Is SOAR suitable for small businesses, or is it only for enterprises?
SOAR platforms are scalable and customizable, making them ideal for organizations of any size. Small businesses offer significant benefits by automating time-intensive tasks, reducing the need for large teams, streamlining operations to improve cost efficiency, and enhancing security posture without requiring extensive in-house expertise.
What kind of tasks can be automated using SOAR?
SOAR automates a wide range of tasks, including phishing analysis to identify and remove malicious emails, threat enrichment by correlating alerts with threat intelligence, incident response such as quarantining infected devices and blocking IP addresses, and compliance reporting by generating detailed reports for audits and regulatory requirements.
What are the challenges of implementing SOAR?
Common challenges include integration complexity, as legacy systems may require additional effort for compatibility; skill requirements, since the initial setup and customization demand expertise; and the risk of over-reliance on automation, where automated actions still require human oversight to avoid false positives.
How does SOAR improve incident response?
SOAR accelerates incident response by leveraging dynamic playbooks that provide standardized workflows for specific threats, real-time data correlation to aggregate and analyze information across tools for actionable insights, and automation to execute containment actions like isolating endpoints or blocking malicious IPs instantly.
How secure is a SOAR platform itself?
Reputable SOAR platforms incorporate robust security and operational features, including encryption to protect data both in transit and at rest, role-based access control to ensure that only authorized users can perform specific actions, and regular updates to address vulnerabilities and enhance functionality.
What industries benefit the most from SOAR?
Industries with high-security demands include financial services, which prioritize protecting sensitive customer data and meeting regulatory requirements; healthcare, where ensuring HIPAA compliance and safeguarding patient information is critical; retail, focused on securing e-commerce platforms and protecting against fraud; and government, tasked with defending against nation-state actors and ensuring the safety of critical infrastructure.
How does SOAR support Zero Trust architectures?
SOAR enhances Zero Trust frameworks by continuously validating user and device credentials, automating micro-segmentation policies, and monitoring and responding to suspicious activities in real-time.
What deployment options are available for SOAR?
SOAR platforms offer deployment options tailored to organizational needs: On-Premises, ideal for organizations with strict data residency and control requirements; Cloud-Based, providing flexibility and scalability for hybrid or fully cloud environments; and Hybrid, blending on-premises control with the scalability and adaptability of the cloud.
How does SOAR enhance team collaboration?
SOAR fosters collaboration by providing Incident War Rooms, virtual spaces where teams can coordinate responses in real-time, along with Task Assignments to delegate responsibilities to specific team members, and Integrated Communication tools like direct messaging and notification systems to streamline teamwork and ensure efficient incident handling
How do you measure the success of a SOAR implementation?
Key metrics for evaluating SOAR effectiveness include a reduction in MTTR (Mean Time to Respond), improved alert accuracy with fewer false positives, enhanced team efficiency through reduced manual workload and faster incident resolution, and significant ROI achieved through cost savings from optimized security operations and minimized breach impact.
What sets Codeguardian.ai’s SOAR apart from competitors?
Customizable playbooks tailored to unique organizational needs, seamless integration with a wide range of tools and systems, scalability to grow alongside your organization, and advanced AI-driven analytics for proactive threat intelligence deliver a comprehensive and adaptive solution for modern security challenges.
What kind of support is available for SOAR users?
At Codeguardian.ai, we provide comprehensive support through 24/7 dedicated assistance for issue resolution and queries, tailored training programs for onboarding and advanced team development, and managed services to deliver end-to-end SOAR platform management for organizations.
How long does it take to implement a SOAR platform?
Implementation timelines for SOAR vary based on several factors, including organization size, integration complexity, and customization needs. Larger organizations may require phased rollouts, while legacy systems and the number of tools to be integrated can also impact timelines. Additionally, developing tailored workflows and playbooks may extend the implementation duration. Overall, deployment timelines typically range from a few weeks to several months.
How can SOAR help with threat hunting?
SOAR enhances threat hunting by automating data collection from logs, endpoints, and network activity, correlating and analyzing this information to identify patterns and anomalies indicative of threats, and streamlining investigations through tools for deep-dive analysis and rapid action.
Can SOAR adapt to emerging threats?
Yes, Codeguardian.ai’s SOAR is built for adaptability, leveraging AI and Machine Learning to continuously improve detection capabilities, utilizing dynamic playbooks that are regularly updated to address new threat vectors, and integrating the latest global threat intelligence feeds. These features demonstrate Codeguardian.ai's expertise and commitment to providing robust, adaptable, and user-centric SOAR solutions.













































